Disclosure: The opinions and opinions expressed right here belong to the authors solely and don’t characterize the views or opinions of the crypto.information editorial.
Because the scandal continues to unfold and consultants have a look at how they strictly compromise our nationwide safety with its sign chat leaks and disgrace themselves by means of controversial post-statements, I want to take a more in-depth have a look at one specific episode of the story.
You may prefer it too: When AI rewrites historical past, blockchain expertise is a line of protection | Opinion
Initially, the White Home denied that chats existed. Nevertheless, when it turned clear that there was an excessive amount of proof to refute, they modified their techniques and denied that the chat contained delicate details about the significance of nationwide safety. And positively, what proof can journalist Jeffrey Goldberg give after leaving that chat? Moreover, chats have been set to self-destruct messages after a sure time frame. Due to this fact, think about a courtroom listening to the place the events have to current proof. The one accessible proof is screenshots, that’s, just about nothing. Such proof is nearly unattainable to confirm.
The reply is fairly easy. If journalists have been cautious to correctly protect such proof. He was in a position to show that he may entry delicate info when he should not have by publishing the hash whole of the encryption of that info. If he hadn’t been within the chat, he would have by no means recognized when and the place he had deliberate to assault Yemen. Sure particulars could also be revealed later, however is it right when the chat happens?
The answer lies in encryption strategies often known as proof of existence with out disclosure. This consists of two primary parts: encryption and trusted timestamps. This may be accomplished manually on the blockchain (if you recognize the method) or by means of quite a lot of purposes and companies that present proof of blockchain-based timestamps.
Here is how the perform works: Write a message (for instance, copy and paste from chat), generate a hash whole for the message, publish it on the blockchain, and retailer the personal key of the tackle used to publish it. Later, you want this personal key to show that it was your tackle (i.e. you personally) that revealed the hash, and due to this fact it’s essential to show that you just had information of the unique message at the moment. Social media accounts could carry out comparable features, however remember that social platforms are centralized techniques.
So, it is – watch out for all journalists who have to show the existence of information sooner or later with out revealing their content material.
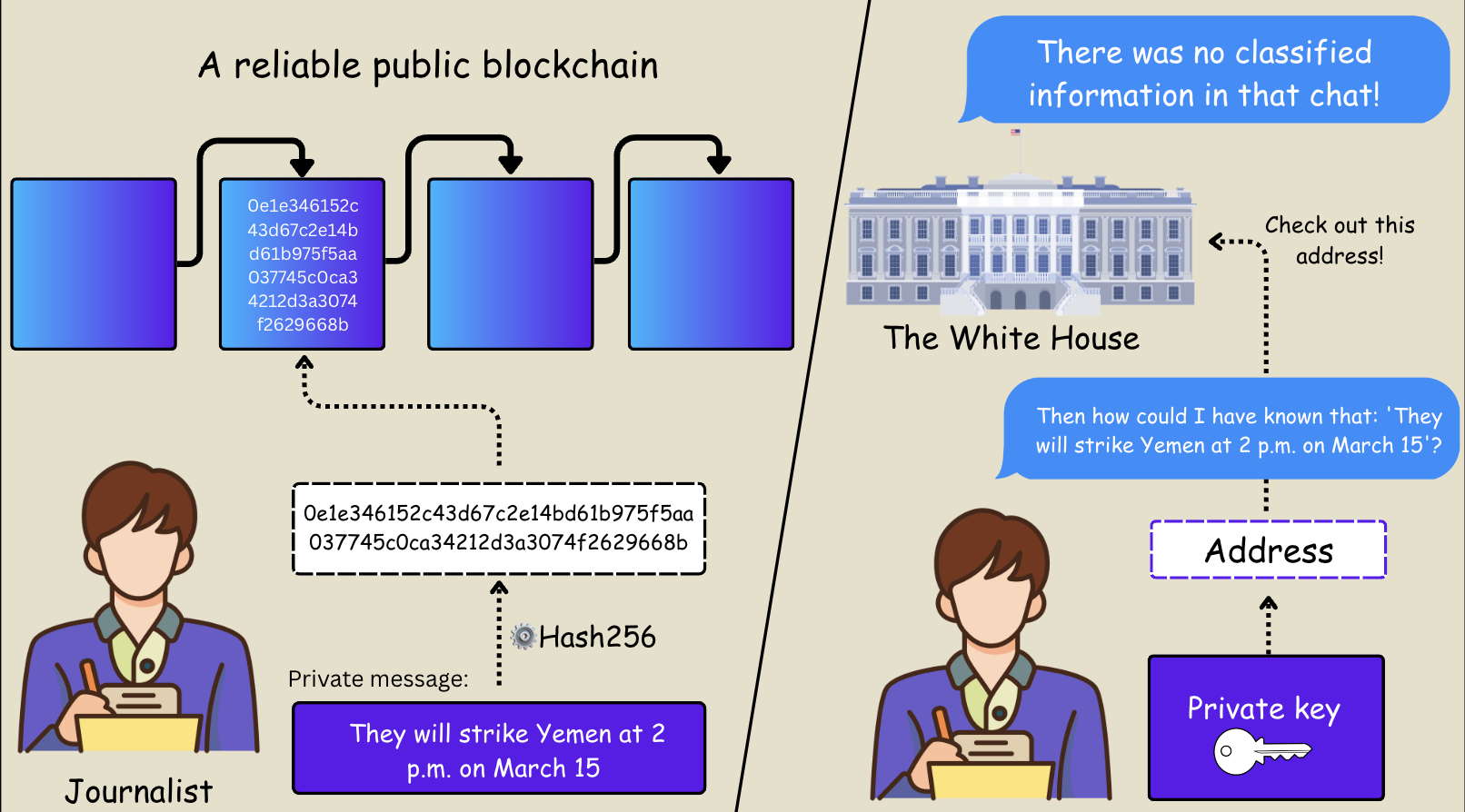
Course of Diagram: Proof of existence utilizing blockchain | Supply: Supplied by the creator
This course of creates a file of simple timestamps that affirm {that a} specific authentic message exists and is thought to the writer on the time the blockchain transaction is confirmed. This did not publish every part till the journalists selected to take action.
learn extra: Past Consensus: Transaction Privateness is the subsequent safety frontier in blockchain | Opinion


